Казино Х – это воплощение лучших достижений мировой индустрии азартных развлечений и играть на автоматах полностью легально. Компания одной из первых получила государственную лицензию. Для регистрации в Casino X созданы рабочие зеркала www.casino-x1.com – официальные копии главного сайта.
Рабочее зеркало казино — это альтернативный адрес сайта казино, который помогает обойти блокировки.
Содержание:
- Регистрация и вход
- Официальный сайт
- Рабочее зеркало
- Ввод и вывод средств
- Бонусы для игроков
- Тех. поддержка
| Основная информация: | |
| Официальный сайт | casinox-club.ru |
| Бонус | 200% на депозит. |
| Год основания | 2012 |
| Валюта счета | Российский рубль, Доллар и др. |
| Способы депозита | Visa, MasterCard, Мир, СБП, Криптовалюты, qr код |
| Способы вывода | Visa, MasterCard, Мир, СБП, Криптовалюты, qr код |
| Язык | Русский, Английский и др. |
Регистрация и вход
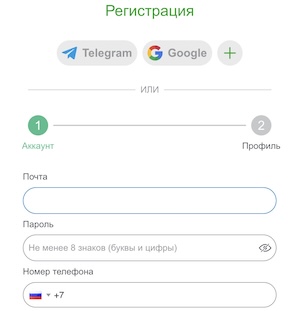
Перед тем как играть в игровые автоматы в онлайн казино Casino-X, пользователям нужно пройти процедуру регистрации. Сделать это можно двумя методами:
- По телефону. Игрок в соответствующей форме вносит информацию о стране, номере собственного мобильного телефона, пароль и промокод. Также пользователь подтверждает, что ему уже исполнилось 18 лет и согласен с правилами и условиями работы на площадке.
- По электронной почте. В этом случае нужно проделать все то же, но вместо телефона вводят актуальный E-Mail.
Далее следует подтвердить номер телефона или электронную почту для дальнейшей авторизации аккаунта.
Форма входа:
Подарки за регистрацию:
| Название | Пpиветственный 200% | Фриспины |
| Миндеп | 500 pyблей | 1 000 pyблей |
| Вейджеp | х30 | х20 |
Официальный сайт
Официальный сайт Казино Х предлагает более тысячи культовых слотов и яркие новинки азартных игр. Casino X регулярно проводит турниры с большим призовым фондом в десятки тысяч рублей, предлагает щедрые бонусы и сервис премиального уровня.
Рейтинг официального сайта:
| Название площадки | Рейтинг |
| Casinoglobal | 9,5 (из 10) |
| Casinotopsonline | 9 (из 10) |
| Trust | 8 (из 10) |
| Latestcasinobonuses | 8,3 (из 10) |
| Casinoking | 9,5 (из 10) |
| Kasino-narubli5 | 4 (из 5) |
| Topcasinoexpert | 8 (из 10) |
| Kazinohi | 4,8 (из 5) |
Рабочее зеркало сайта

Рабочее зеркало казино — это альтернативный адрес сайта казино, который используется для обхода блокировок и ограничений доступа к основному сайту.
В некоторых странах, включая Россию, деятельность онлайн-казино может быть запрещена или ограничена. В таких случаях провайдеры интернета блокируют доступ к сайтам казино. Чтобы обойти эти блокировки, казино создают зеркала — копии своего сайта, доступные по другому адресу.
Этот бренд имеет оффшорную лицензию, поэтому вход может быть заблокирован для пользователей. Также, вход на сайт может быть ограничен профилактическими работами. Для того чтобы обойти блокировку, разработчики позаботились об альтернативной версии. Она ничем не отличается от оригинала, кроме адреса сайта. Информацию о зеркале можно запросить у администрации заведения.
Сохраните несколько актуальных vip зеркал:
| casinox-club.ru | casino-x777.ru |
| 24casino-x.ru | casinox888.ru |
| x-casino-x-online.com | casino-x.com |
| onlinexcasino.org | casino-x7.ru |
| ru.casino-x.com | www.casino-x.com |
Способы депозита и вывода средств
Казино Икс позволяет своим игрокам играть на разные валюты, игроки могут производить пополнение счета в долларах, рублях и евро. Для пополнения счета и вывода средств рекомендуется использовать одну и ту же платежную систему. Игрокам предлагаются следующие способы ввода:
- Банковские карты (Visa или MasterCard, в некоторых казино Visa Electron и Maestro также принимаются).
- Интернет-банкинг – это самый удобный способ.
- Терминалы – например IBOX и СИСТЕМА.
- Электронные кошельки – системы QIWI и WebMoney не рекомендуются, лучше использовать кошелек Global 24, позволяющий вносить деньги со счетов мобильных операторов.
- СМС по телефону.
- Криптовалюта – многие онлайн заведения предлагают этот метод.
Необходимо учитывать, что любая платежная система имеет свои лимиты суммы транзакций.
Также необходимо знать, что есть лимиты не только на ввод средств, но и вывод. Если пользователь планирует играть и вывести их на деньги, он должен понимать, что заявку на вывод можно создать, только начиная с определенной суммы.
При осуществлении операций по пополнению и выводу средств следует учитывать размер комиссии, которую устанавливает платежная система. Минимальная доступная сумма для вывода составляет 250 рублей.
Следует также знать, что неотыгранные бонусные средства при каждом выводе будут аннулированы.
Бонусы

Казино Х имеет бонусную программу, мотивирующую новых пользователей зарегистрироваться и действующих клиентов стать более активными. Условия получения бонусов, таких как приветственный бонус Welcome Pack, зависят от суммы пополнения и могут включать фриспины.
Ниже перечислены бонусы, которые игроки могут получить при совершении депозитов и соответствующего отыгрыша в соответствии с условиями:
- Бонус на депозит №1: 100% бонусов и 25 бесплатных вращений, минимальный депозит – 250 рублей, вейджер – 25, максимальная сумма бонуса – 300.
- Бонус на депозит №2: 125% бонусов и 50 бесплатных вращений, минимальный депозит – 300, вейджер – 25, максимальная сумма бонуса – 1500.
- Бонус на депозит №3 (хит): 150% бонусов и 100 бесплатных вращений, минимальный депозит – 500, вейджер – 25, максимальная сумма бонуса – 20000.
Чтобы получить выигрыш от бонуса в живой монете, нужно отыграть полученную сумму не менее 30 раз. У бонусов есть определенные условия, такие как указанный слот и дедлайн для отыгрыша. Бездепозитные бонусы не предоставляются, но можно воспользоваться промокодами, которые можно приобрести за баллы в программе лояльности.
Техподдержка
Самый простой способ получить помощь — написать в чат.
- Владелец: Pomadorro N.V.
- Live Chat: Да
- E-mail: ru_support@casino-x.com
Это надежное казино, которому можно доверять. Здесь есть высокие шансы на выигрыш, отличный качественный скрипт и наличие лицензии. Все работает безупречно, слоты загружаются быстро и без зависаний. Что касается бонусов, сайт предлагает очень хорошие условия — вы можете получить до 500 долларов бонуса.
Это одно из самых высококачественных казино, где я играл на реальные деньги. Здесь функционал находится на высоком уровне, игровые автоматы работают без сбоев и зависаний. Программы для автоматов не подкручиваются против игрока, поэтому у вас есть реальные шансы на выигрыш. Я лично уже несколько раз удачно сорвал неплохой куш здесь.
В данном игровом заведении вы найдете все необходимое: разнообразные игры, бонусные предложения и турниры. Одним из главных преимуществ является то, что сразу после регистрации вы получаете бонус, который можно использовать для игры на игровых автоматах.
Я недавно начал играть в казино икс и уже вижу хорошие результаты. У меня были отличные выигрыши, хорошая бонусная программа для новых игроков и быстрый вывод денег.